
Phishing
Cyber criminals love phishing. Unfortunately, this is not a harmless riverbank pursuit. When criminals go
phishing, you are the fish and the bait is usually contained in a scam email, text message or via a social media communication. Phishing emails can reach millions of users directly, attacks can install malware (such as ransomware), sabotage systems, or steal intellectual property and money.
Organisations of any size and type as well as individuals can be hit.
Mass campaigns is where the attacker is looking to collect passwords or make easy money, but a targeted attack against an organisation is where the aim is more specific, like the theft of sensitive data. In a targeted attack, the attackers may use information about an organisation or its employees to make messages more persuasive and realistic; known as SPEAR PHISHING.
In an email phishing scam, the attacker sends an email that looks legitimate, designed to trick the recipient into entering information in reply or on a site that the hacker can use to steal or sell their data.
Vishing, which is short for “voice phishing,” is when someone uses the phone to try to steal information. The attacker may pretend to be a trusted friend or relative or to represent them. Also, Smishing which is done via Text
Spear phishing involves targeting a specific individual in an organization to try to steal their login credentials. The attacker often first gathers information about the person before starting the attack, such as their name, position, and contact details.
A whaling attack is a phishing attack that targets a senior executive. These individuals often have deep access to sensitive areas of the network, so a successful attack can result in access to valuable info.
An HTTPS phishing attack is carried out by sending the victim an email with a link to a fake website. The site may then be used to fool the victim into entering their private information.
Social engineering attacks pressure someone into revealing sensitive information by manipulating them psychologically.
With a Machine/man-in-the-middle attack, the hacker gets in “the middle” of two parties and tries to steal information exchanged between them, such as account credentials.

Training
Help by training users how to identify and report suspected phishing emails – Responding to emails and clicking on links is a part of the modern workplace. Spotting phishing emails is hard, and spear phishing is even harder to detect.
Additional Technical Defences
Make it harder for emails from your domains to be spoofed by employing the anti-spoofing controls: DMARC, SPF and DKIM, and encourage your contacts to do the same.
Rapid Incident Response/Disaster
Recovery Plans -All organisations will experience security incidents at some point. Organisations need to detect them quickly, and respond in a planned way. Knowing
about an incident sooner rather than later limits the harm it can cause. Protect your organisation from the effects of undetected phishing emails by having a plan to minimise and recover from the impact of
undetected phishing emails. Please get in touch with WMRCCU at wmcyber@west-midlands.pnn.police.uk for help and incident response planning guidance.
Report
Check out the WMRCCU YouTube Live Video “Spotted a Suspicious Email? What to do with phishing emails. https://youtu.be/fOMbZsRILdc.
The NCSC has launched the pioneering ‘Suspicious Email Reporting Service’, which will make it easy for people to forward suspicious emails to the NCSC – including
those claiming to offer services related to coronavirus. Email: report@phishing.gov.uk
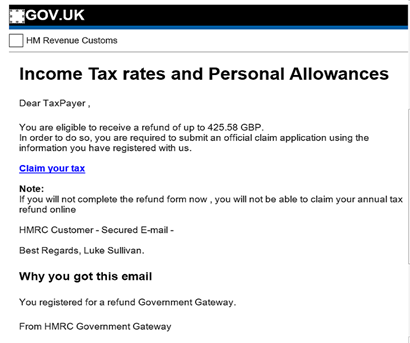
Phishing example
These come in different forms, however, this is just one example. You recieve an email stating your due a refund.
You then click on the link taking you to a website which looks very real. You then enter personal details which include bank details.
The details are then sent to the threat actors.
